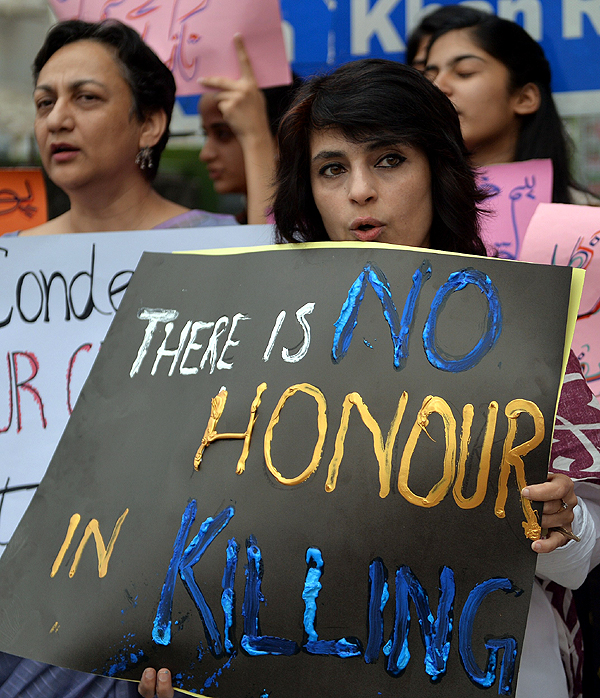This article is a continuance of ‘The Jerusalem Syndrome – Part 2.’ Artemio Vitores, Franciscan Custodian of Holy Land, many Christians believed that the passage through life changing Jerusalem, because "the holy places put you in connection with God," but believes the syndrome is another thing, which are isolated cases . "Coming to Jerusalem is […]
Apr 11 2012 | Posted in
World |
Read More »

This article is a continuance of ‘The Jerusalem Syndrome – Part 1.’ In any culture it is difficult to draw a dividing line that separates sanity from insanity, here in Jerusalem, deciding when mysticism leads to psychosis is a mission that borders on the impossible. For people who would live elsewhere admitted to a psychiatric, […]
Apr 10 2012 | Posted in
World |
Read More »
Normal 0 false false false EN-GB X-NONE X-NONE MicrosoftInternetExplorer4 /* Style Definitions */ table.MsoNormalTable {mso-style-name:”Table Normal”; mso-tstyle-rowband-size:0; mso-tstyle-colband-size:0; mso-style-noshow:yes; mso-style-priority:99; mso-style-qformat:yes; mso-style-parent:””; mso-padding-alt:0in 5.4pt 0in 5.4pt; mso-para-margin-top:6.0pt; mso-para-margin-right:0in; mso-para-margin-bottom:0in; mso-para-margin-left:0in; mso-para-margin-bottom:.0001pt; mso-pagination:widow-orphan; font-size:11.0pt; font-family:”Calibri”,”sans-serif”; mso-ascii-font-family:Calibri; mso-ascii-theme-font:minor-latin; mso-fareast-font-family:”Times New Roman”; mso-fareast-theme-font:minor-fareast; mso-hansi-font-family:Calibri; mso-hansi-theme-font:minor-latin;} Apple, Inc. made the news last week when it all came down to […]
Apr 9 2012 | Posted in
Sci-Tech |
Read More »
There were times when Mac machines were considered one of the most secure platforms in the world, if not the most secure. However, gone are the days when users could blind trust Apple products in terms of secure operating systems. The main reason attached to such vulnerability to malware attacks is the sales of Mac […]
Apr 9 2012 | Posted in
Sci-Tech |
Read More »
“Wait until HTML5 becomes more ubiquitous for similar types of threat vulnerabilities, and you can have a botnet that runs in your browser,” Ferguson cautioned. “The more ubiquitous these platforms are, it won’t matter if it’s a mobile device or a computer. It it’s running Java or any other cross-platform technology, the threat is there.” […]
Apr 9 2012 | Posted in
Sci-Tech |
Read More »